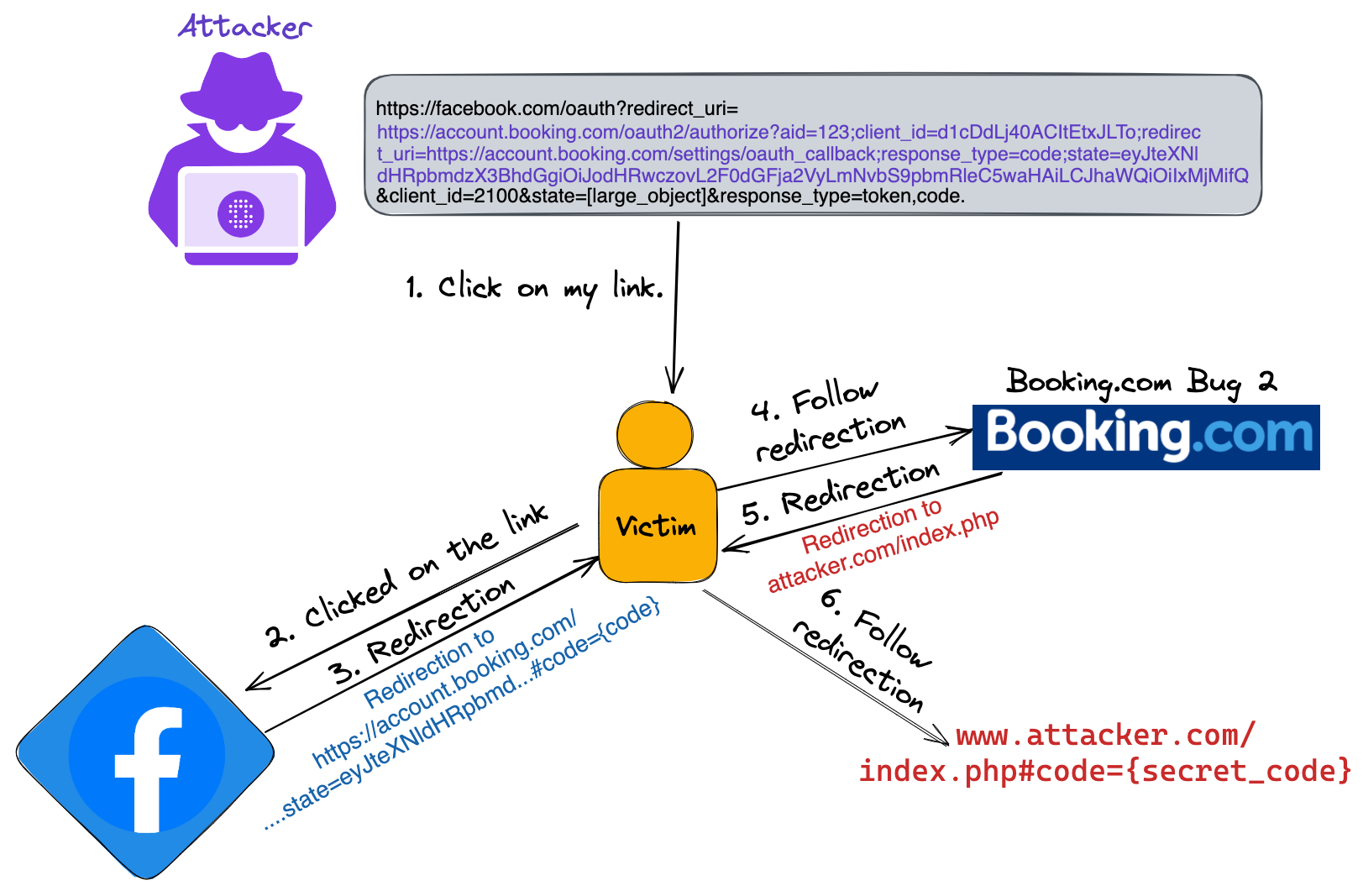
OAuth Vulnerabilities
What is OAuth 2.0? OAuth 2.0 is an open standard for authorization that allows users to grant third-party applications limited access to their resources hosted on another service, without exposing ...

What is OAuth 2.0? OAuth 2.0 is an open standard for authorization that allows users to grant third-party applications limited access to their resources hosted on another service, without exposing ...

What is OAuth 2.0? OAuth 2.0 is an open standard for authorization that allows users to grant third-party applications limited access to their resources hosted on another service, without exposing ...

Introduction to SQL Injection SQL Injection is one of the most common and potentially devastating vulnerabilities in web applications. It occurs when an attacker manipulates SQL queries by injectin...
.png)
Hello everyone, it’s Ujwal Rathor back with an exciting update! With August in full swing, it's the perfect time to start planning your participation in some of the most thrilling hackathons...

Graduating and stepping into the professional world can be daunting, but knowing which exams to target can make the journey smoother. Leading companies like TCS, Infosys, Wipro, and others have spe...
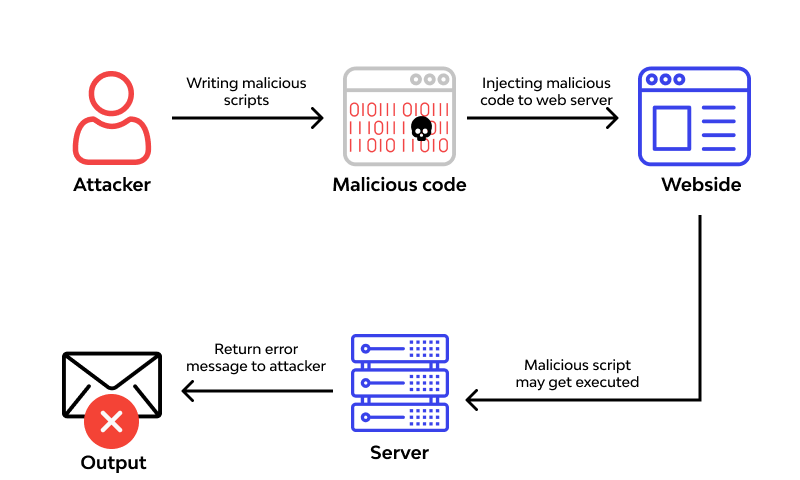
What is RCE? Remote Code Execution (RCE) is a critical security vulnerability that allows an attacker to execute arbitrary code on a remote machine over the internet. This can lead to full control ov...

What is LFI? Local File Inclusion (LFI) is a type of security vulnerability found in web applications. It happens when an attacker tricks a website into displaying or running files from the server t...
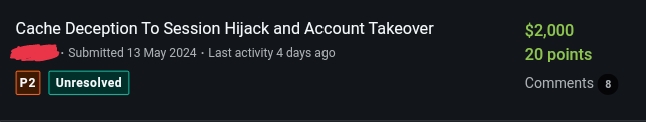
What is Web Cache Deception? Web cache deception occurs when discrepancies between cache proxies and backend servers lead to dynamic content being mistakenly cached and served as static content....

Last year, Ilya Sutskever was the name everyone associated with genius in the AI world. As a co-founder of OpenAI and a key figure in the creation of the groundbreaking AlexNet convolutional neural ne...
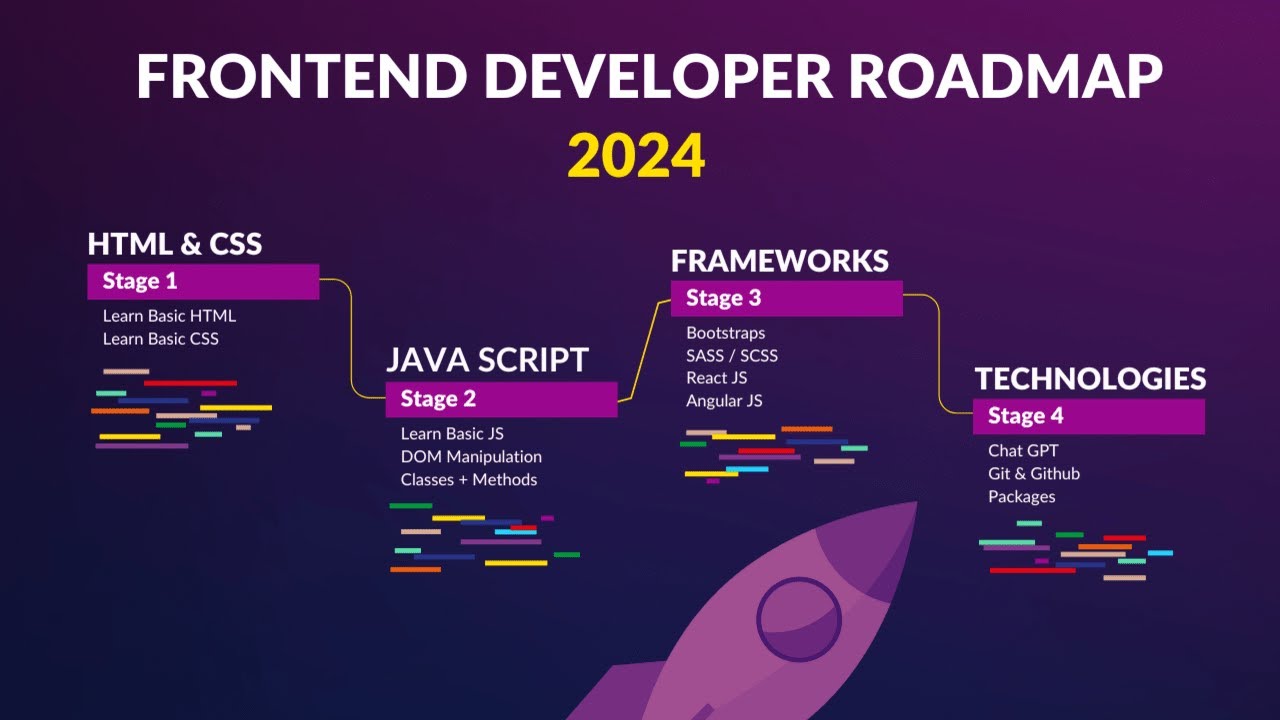
Hello friends, I am Sachin Kumar Mandal. Today, I am sharing a detailed Frontend Developer Roadmap to help you become a proficient frontend developer. Follow this step-by-step guide to know what to st...