Remote Code Execution (RCE) Vulnerabilities
What is RCE?
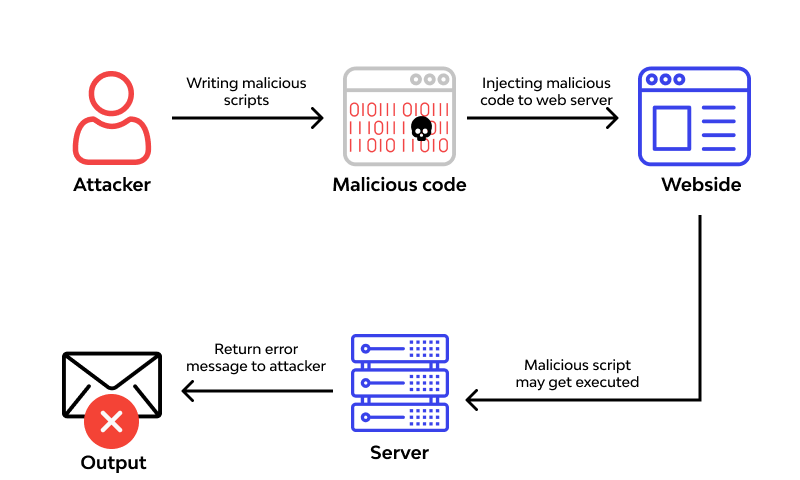
Remote Code Execution (RCE) is a critical security vulnerability that allows an attacker to execute arbitrary code on a remote machine over the internet. This can lead to full control over the compromised system, data breaches, and severe damage to the organization’s infrastructure.
How Does RCE Work?
RCE vulnerabilities typically occur due to poor input validation or improper handling of user input in applications. Here’s a simplified breakdown of how RCE might happen:
1. User Input: An application receives input from a user, such as a form submission, file upload, or URL parameter.
2. Improper Handling: The application processes this input without proper validation or sanitization.
3. Code Execution: If the input includes malicious code, the application might execute it, leading to unintended actions.
For example, consider a web application that accepts a filename as input to display its contents:
http://example.com/viewfile?name=report.txt
If the application doesn't properly sanitize this input, an attacker might change the URL to:
http://example.com/viewfile?name=report.txt;rm -rf /
In this case, if the server executes the input directly, it might run the malicious command rm -rf /, which deletes all files on the server.
Why is RCE Dangerous?
1. Full System Compromise: Attackers can gain complete control over the affected system.
2. Data Theft: Sensitive data can be stolen, leading to privacy breaches.
3. System Damage: Attackers can delete or alter files, disrupting services and causing data loss.
4. Propagation: RCE vulnerabilities can be used to spread malware or ransomware.
Common Causes of RCE
1. Unsanitized User Input: Not properly validating or sanitizing input before processing.
2. Deserialization Issues: Unsafe deserialization of untrusted data.
3. Insecure Code Execution Functions: Using functions that execute code or commands based on user input without proper checks.
4. Outdated Software: Running outdated software with known vulnerabilities.
Preventing RCE Vulnerabilities
Input Validation and Sanitization:
1. Validate and sanitize all user inputs rigorously.
2. Use allow-lists to permit only specific, expected inputs.
Secure Coding Practices:
1. Avoid using dangerous functions like eval(), exec(), or system().
2. Use parameterized queries and prepared statements.
Regular Updates and Patching:
1. Keep all software and dependencies updated to mitigate known vulnerabilities.
2. Regularly apply security patches.
Security Testing:
1. Conduct regular security audits and penetration testing.
2. Use static and dynamic code analysis tools to identify potential vulnerabilities.
Least Privilege Principle:
1. Run applications with the minimum necessary privileges.
2. Use containerization and sandboxing to isolate applications.


🙌
👌🔥