OAuth Vulnerabilities
What is OAuth 2.0?
OAuth 2.0 is an open standard for authorization that allows users to grant third-party applications limited access to their resources hosted on another service, without exposing their credentials. Unlike traditional authentication, where users share their credentials directly with an application, OAuth 2.0 enables a secure, token-based approach that separates authentication from authorization.
Key Concepts in OAuth 2.0
Resource Owner: The entity that owns the data or resource, usually the end-user.
Client: The application requesting access to the resource on behalf of the resource owner. The client can be a web app, mobile app, or any other service.
Authorization Server: The server that authenticates the resource owner and issues access tokens to the client. It ensures that the client is authorized to access the resource.
Resource Server: The server hosting the protected resource. It accepts and validates access tokens provided by the client before granting access to the resource.
Access Token: A credential that the client uses to access protected resources on the resource server. Access tokens have a limited lifespan and scope, meaning they only grant access to specific resources for a set period.
How OAuth 2.0 Works
OAuth 2.0 operates through a series of steps that involve the client, the resource owner, the authorization server, and the resource server. Here's a simplified overview of the OAuth 2.0 flow:
Authorization Request: The client initiates the process by redirecting the resource owner to the authorization server, typically through a login or consent screen. The client requests permission to access specific resources on behalf of the user.
Authorization Grant: If the resource owner approves the request, the authorization server provides an authorization grant to the client. This grant could be in the form of an authorization code, implicit grant, resource owner password credentials, or client credentials.
Token Exchange: The client exchanges the authorization grant with the authorization server to obtain an access token. Depending on the flow, the client might also receive a refresh token that can be used to obtain a new access token when the current one expires.
Access Resource: The client uses the access token to request the protected resource from the resource server. The resource server validates the token and, if valid, grants the client access to the requested resource.
Token Expiry and Refresh: Access tokens are typically short-lived to minimize security risks. When an access token expires, the client can use a refresh token (if available) to obtain a new access token without requiring the resource owner to reauthorize.
OAuth 2.0 Grant Types
OAuth 2.0 supports multiple grant types, each suited for different use cases:
Authorization Code Grant: This is the most secure and commonly used flow, ideal for server-side applications. It involves an intermediate step where the client exchanges an authorization code for an access token.
Implicit Grant: Designed for public clients, such as single-page applications (SPAs), this flow directly issues an access token without an intermediate authorization code exchange. It is less secure and typically recommended only when necessary.
Resource Owner Password Credentials Grant: This flow allows the client to collect the resource owner's credentials (username and password) and exchange them directly for an access token. It's typically used when the client is highly trusted, such as in first-party apps.
Client Credentials Grant: This flow is used for machine-to-machine communication, where the client authenticates using its credentials without involving a resource owner.
Introduction
OAuth is a widely-used protocol for authorization that enables applications to access resources on behalf of a user without exposing their credentials. While OAuth provides a flexible and secure way to handle authentication and authorization, improper implementation can introduce vulnerabilities. This blog will explore common OAuth vulnerabilities, their potential impact, and best practices to secure your OAuth implementation.
Common OAuth Vulnerabilities
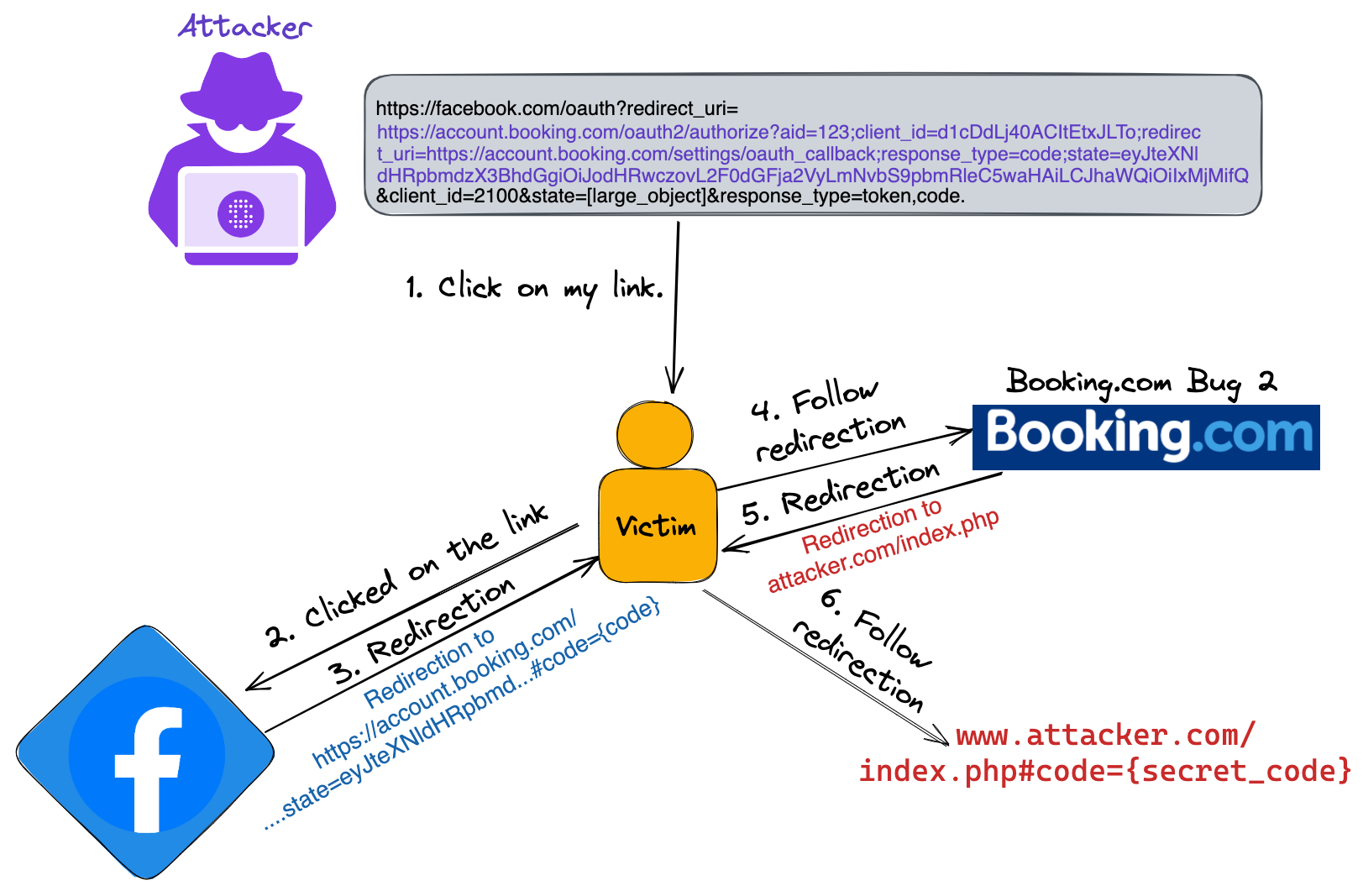
1.Misconfigured Redirect URIs
Issue: One of the most critical vulnerabilities in OAuth is improper handling of redirect URIs. Attackers can exploit open redirect issues to trick users into giving access to malicious sites, leading to phishing attacks and unauthorized access.
Solution: Always validate redirect URIs. Ensure that only pre-registered and trusted URIs are allowed, and avoid using wildcards that could enable arbitrary redirection.
2.CSRF (Cross-Site Request Forgery)
Issue: OAuth flows are susceptible to CSRF attacks, where an attacker tricks a user into unknowingly initiating an OAuth authorization flow, which could result in unauthorized actions.
Solution: Implement CSRF protection by using state parameters in your OAuth requests. This parameter should be unique for each session and validated on return to ensure that the request is legitimate.
3.Token Leakage
Issue: OAuth tokens, if exposed, can grant attackers unauthorized access to user resources. Token leakage can occur due to insecure storage, transmission, or improper handling of tokens.
Solution: Securely store tokens using encryption and transmit them over HTTPS. Implement short-lived tokens with frequent rotation and consider using refresh tokens to limit exposure.
4.Issue: OAuth tokens that cannot be revoked pose a significant security risk, as they remain valid until they expire. If a token is compromised, the attacker can continue accessing resources without restriction.
Solution: Implement token revocation mechanisms that allow users or administrators to invalidate tokens immediately. Ensure that the API or resource server respects token revocation.
5.Inadequate Scopes
Issue: Over-permissive scopes can lead to excessive access to user resources. If an application requests more permissions than necessary, a compromised token could cause significant damage.
Solution: Follow the principle of least privilege. Define and request the minimum scopes required for the application's functionality, and educate users on the implications of granting specific permissions.
6.Replay Attacks
Issue: In replay attacks, an attacker captures and reuses a valid OAuth token to gain unauthorized access to resources.
Solution: Use nonce or timestamp mechanisms to ensure that each token or request is unique and cannot be reused. Implement secure session management practices.
Here are some Oauth reports
https://hackerone.com/reports/131202
https://hackerone.com/reports/6017
https://hackerone.com/reports/7900
https://hackerone.com/reports/244958
https://hackerone.com/reports/405100


Great insights on OAuth vulnerabilities