
SQL Injection Vulnerabilities
Introduction to SQL Injection SQL Injection is one of the most common and potentially devastating vulnerabilities in web applications. It occurs wh...
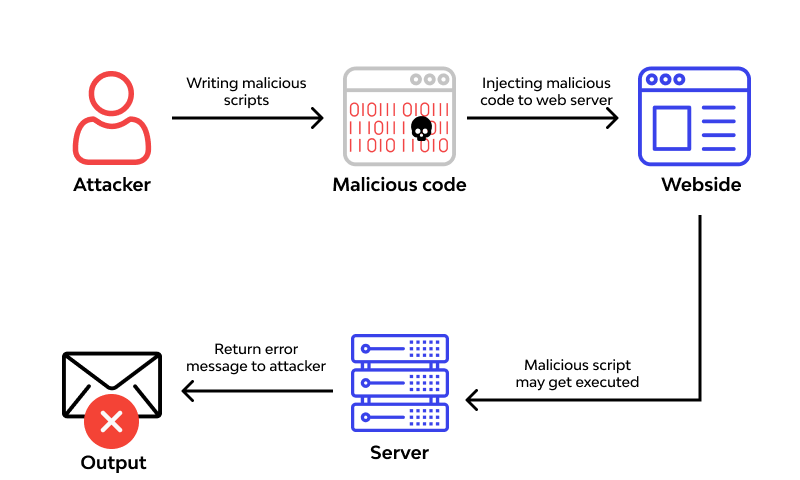
Remote Code Execution (RCE) Vulnerabilities
What is RCE? Remote Code Execution (RCE) is a critical security vulnerability that allows an attacker to execute arbitrary code on a remote machine o...

Local File Inclusion (LFI) Vulnerabilities
What is LFI? Local File Inclusion (LFI) is a type of security vulnerability found in web applications. It happens when an attacker tricks a website ...
How I Made $2000 Hacking CDN Caching Servers
What is Web Cache Deception? Web cache deception occurs when discrepancies between cache proxies and backend servers lead to dynamic content bei...

Insecure Direct Object References (IDOR) Vulnerabilitie
What is IDOR Insecure Direct Object Reference (IDOR) occurs when an application provides direct access to objects based on user-supplied input and ...
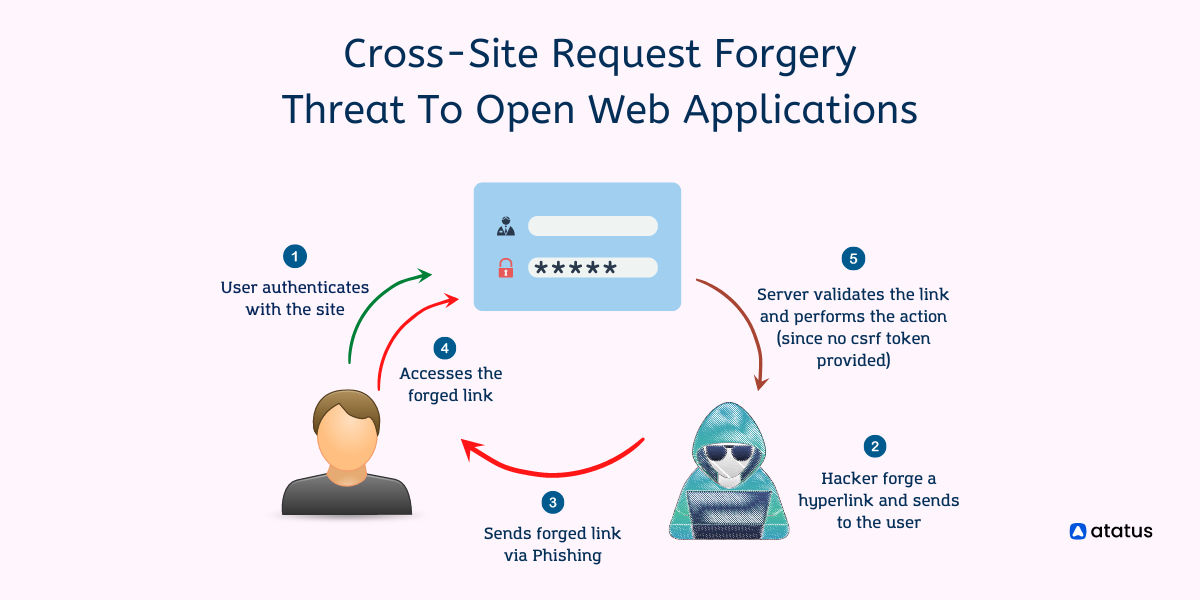
Cross-Site Request Forgery (CSRF) Vulnerabilities
In today's interconnected web, security threats are a constant concern. Among various security vulnerabilities, Cross-Site Request Forgery (CSR...
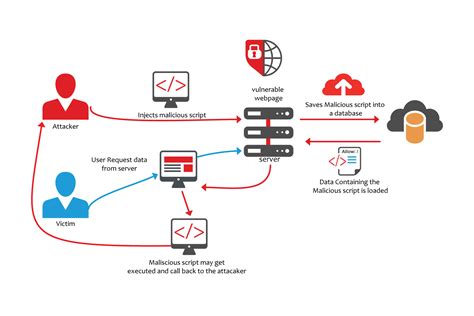
Protecting Your Website from XSS Vulnerabilities
Introduction Hello everyone, My name is Samark, and I am currently a student at DSPMU College, where I am in my 4th semester. I have developed a s...
