Cross-Site Request Forgery (CSRF) Vulnerabilities
In today's interconnected web, security threats are a constant concern. Among various security vulnerabilities, Cross-Site Request Forgery (CSRF) is a significant and often misunderstood threat. This post will delve into what CSRF is, how it works, and how you can protect your applications from it.
What is CSRF?
Cross-Site Request Forgery (CSRF) is a type of attack that tricks a user into performing actions on a web application in which they are authenticated, without their knowledge or intent. These actions can range from changing account details to making unauthorized transactions.
How Does CSRF Work?
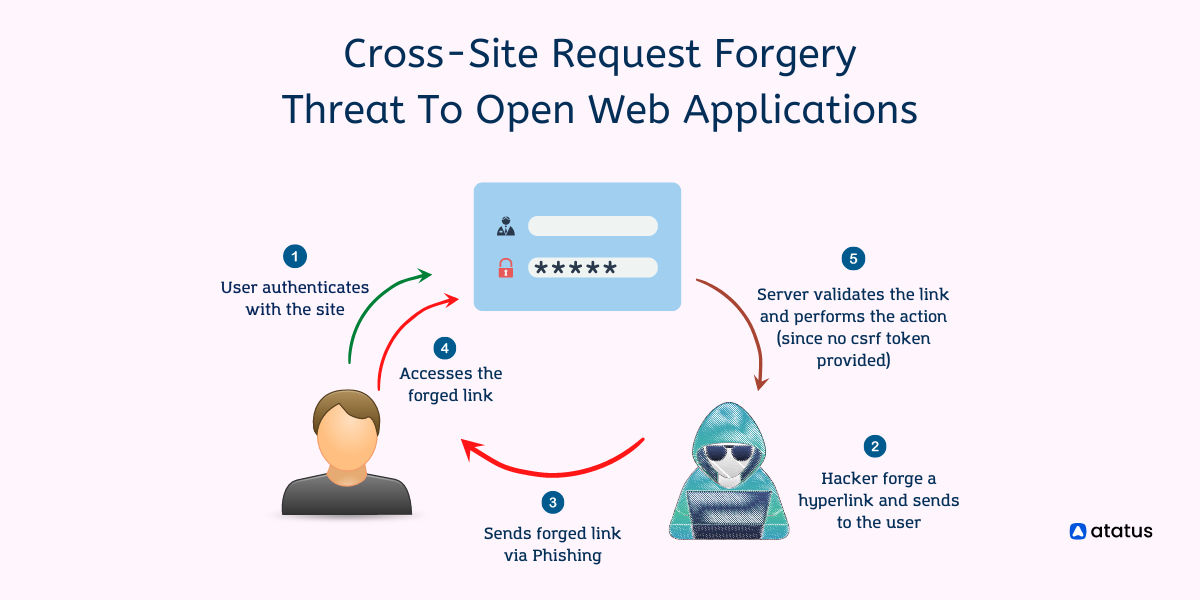
1. Victim Authentication: The user logs into a web application and receives a session cookie, which is used to authenticate future requests.
2. Malicious Request Creation: An attacker crafts a malicious request to the web application. This request could be embedded in an email, a website, or any form of online communication.
3. User Interaction: The user unknowingly interacts with the malicious link or form. This interaction triggers the malicious request.
4. Request Execution: Since the user is already authenticated, the web application processes the malicious request as if it were legitimate, performing the action specified by the attacker.
Example Scenario
Imagine a banking application where users can transfer funds. An attacker creates a malicious link like this:
a href="https://www.examplebank.com/transfer?amount=1000&toAccount=attacker123" Click here for a free gift!
When a logged-in user clicks this link, their browser sends a request to the bank's server to transfer $1000 to the attacker's account, exploiting the user's authenticated session.
Protecting Against CSRF
To defend against CSRF attacks, developers can implement several strategies:
1. CSRF Tokens
A CSRF token is a unique, secret, and unpredictable value generated by the server and included in each form submission or state-changing request. The server verifies the token before processing the request.
Implementation:
Generate Token: Create a unique token and store it in the user's session.
Embed Token: Include the token in HTML forms or as a hidden field.
Verify Token: On receiving a request, check if the token matches the one stored in the session.
2. SameSite Cookies
The SameSite attribute in cookies restricts how cookies are sent with cross-site requests, providing some protection against CSRF.
Implementation:
Set Cookie Attribute: Configure session cookies with SameSite=Lax or SameSite=Strict.
Set-Cookie: sessionId=abc123; SameSite=Strict;
3. Double Submit Cookies
This technique involves sending the CSRF token both as a cookie and as a request parameter. The server compares the token in the cookie with the token in the request.
4. Custom Request Headers
Only allow state-changing requests (like POST, PUT, DELETE) to be made via AJAX with custom headers. Since cross-origin requests cannot set custom headers without CORS preflight, this prevents CSRF attacks.
Implementation:
Set Custom Header: Include a custom header in AJAX requests.
Verify Header: Ensure the server validates the presence of the custom header.
Conclusion
CSRF is a potent attack vector that exploits the trust a web application places in a user's browser. By understanding how CSRF works and implementing robust protection mechanisms like CSRF tokens, SameSite cookies, double submit cookies, and custom request headers, you can safeguard your web applications against this threat. Stay vigilant and continuously review your security measures to ensure they are up to date and effective against evolving threats.


🐞🔥
This is very important at this time
Keep it up 👍